In today’s hyper-connected world, messaging apps have become an indispensable part of our daily lives. We use them for everything from casual chats with friends to important business communications. However, many traditional messaging services rely on outdated technology that leaves …
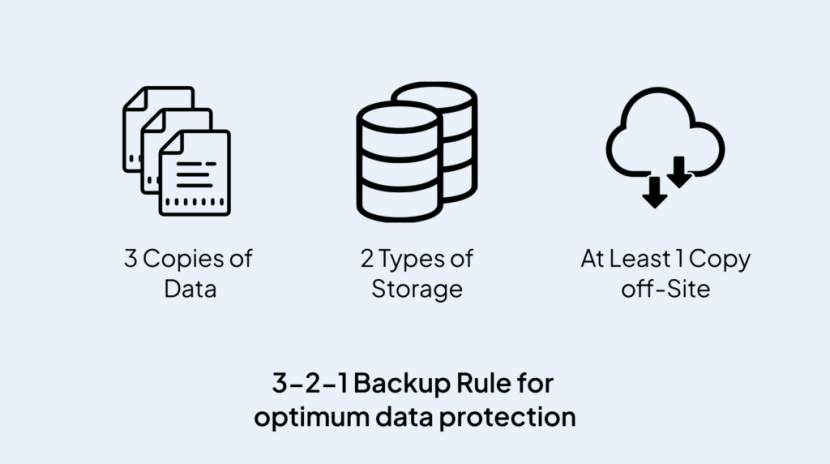
The Imperative of Data Backup: Implementing the 3-2-1 Rule for Comprehensive Protection
In the digital era, where data has become an invaluable asset, safeguarding its integrity and accessibility is paramount. The 3-2-1 rule of data backup serves as a robust strategy to ensure the resilience of your critical information in the face …
Bitdefender: Your Trusted Partner in Online Security
As the digital age accelerates, so does the need for reliable and effective cybersecurity solutions. Bitdefender Internet Security stands out as the undisputed leader in online protection, providing peace of mind and safeguarding your digital presence. Trusted by millions of …
McAfee’s Decline: A Once-Dominant Antivirus Loses Its Edge
McAfee, once a leading name in antivirus software, has experienced a significant decline in recent years. Several factors have contributed to its diminished reputation. 1. Performance Issues: McAfee’s antivirus software has been criticized for being resource-intensive, often slowing down systems, …
The Decline of Norton Antivirus: Is It Still Worth It?
Norton Antivirus, once a stalwart in the realm of cybersecurity, has seen a decline in recent years. While it still offers protection, its reputation has taken a hit due to several factors. 1. Resource-Intensive: Norton’s deep scanning and real-time protection …

Social Engineering: The Art of Manipulation
Social engineering is a type of attack that exploits human psychology to gain access to confidential information or systems. It’s a technique that relies on manipulating people into revealing sensitive data or performing actions that can compromise their security. Unlike …

Phishing Attacks: A Growing Threat to Your Online Security
Phishing attacks are a common form of cybercrime where scammers attempt to trick individuals into divulging sensitive information like passwords, credit card numbers, or personal data. These attacks often involve emails or messages that appear to be from legitimate sources, …
Malware: A Threat to Your Digital World
Malware, short for malicious software, is a broad term encompassing any software designed to harm computer systems, networks, or data. It can range from simple viruses to complex ransomware that can cripple entire organizations. Understanding how malware works and how …
Today we learn about email phishing.
By staying vigilant and recognizing the hallmarks of phishing scams, you can significantly reduce the risk of falling victim to these cyberattacks. If you need help identifying emails and text messages as scams, call, text, or email One Stop Support …
PSA Post about common Facebook scam!
I hate that we have to be so vigilant on social media, but unfortunately there are scams all over the place. I’ve talked about this particular approach before, but it has continued to become incredibly popular over the last couple …
