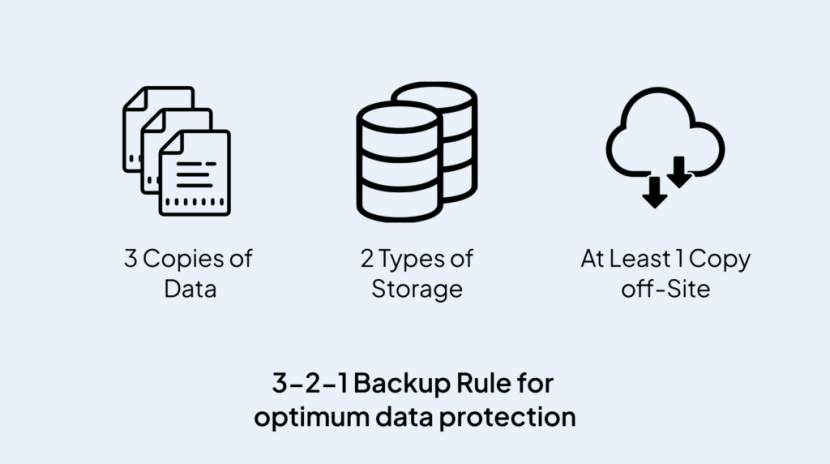
In the digital era, where data has become an invaluable asset, safeguarding its integrity and accessibility is paramount. The 3-2-1 rule of data backup serves as a robust strategy to ensure the resilience of your critical information in the face …
Tech Support Made Simple

In the digital era, where data has become an invaluable asset, safeguarding its integrity and accessibility is paramount. The 3-2-1 rule of data backup serves as a robust strategy to ensure the resilience of your critical information in the face …
McAfee, once a leading name in antivirus software, has experienced a significant decline in recent years. Several factors have contributed to its diminished reputation. 1. Performance Issues: McAfee’s antivirus software has been criticized for being resource-intensive, often slowing down systems, …
Norton Antivirus, once a stalwart in the realm of cybersecurity, has seen a decline in recent years. While it still offers protection, its reputation has taken a hit due to several factors. 1. Resource-Intensive: Norton’s deep scanning and real-time protection …

The truth about those so-called performance enhancers. In the realm of technology, myths often persist, and one such myth revolves around PC performance boosters. These software programs claim to magically speed up your computer, but are they truly effective? Let’s …

Social engineering is a type of attack that exploits human psychology to gain access to confidential information or systems. It’s a technique that relies on manipulating people into revealing sensitive data or performing actions that can compromise their security. Unlike …

Phishing attacks are a common form of cybercrime where scammers attempt to trick individuals into divulging sensitive information like passwords, credit card numbers, or personal data. These attacks often involve emails or messages that appear to be from legitimate sources, …

Computers have come a long way from the room-sized behemoths of the past. Today, we have a diverse range of machines catering to various needs and preferences. Let’s delve into the world of different computer styles, exploring their strengths and …

The computer sits on your desk, humming contentedly, but have you ever wondered what goes on inside that sleek case? Fear not, curious minds! This article will unveil the essential components that work together to bring your digital world to …
The computer, once a marvel of science fiction, is now an everyday tool used for work, entertainment, and communication. But for those unfamiliar with its inner workings, it can seem like a complex and intimidating machine. Fear not! This article …