Check out our latest project. We’re trying to provide a better platform to compete with the nuisance and excessive advertisements on Facebook and all Meta brands of social media. We’re avoiding showing ads between every other post, or trying to …
Why RCS and End-to-End Encryption Matter for Your Messages
In today’s hyper-connected world, messaging apps have become an indispensable part of our daily lives. We use them for everything from casual chats with friends to important business communications. However, many traditional messaging services rely on outdated technology that leaves …
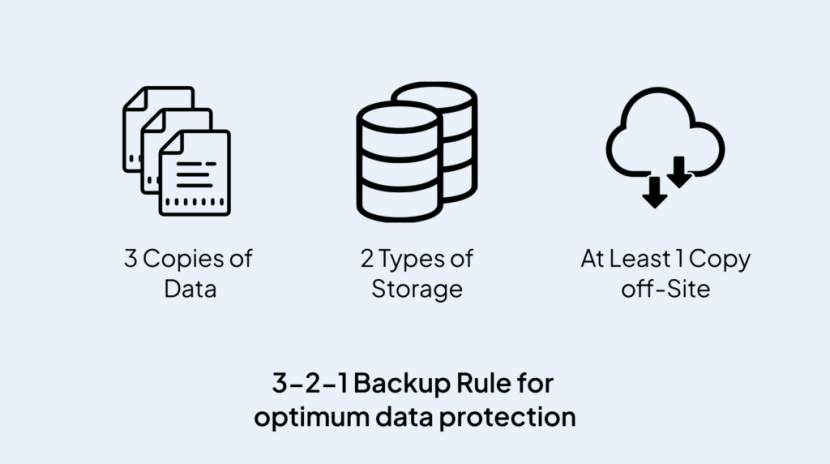
The Imperative of Data Backup: Implementing the 3-2-1 Rule for Comprehensive Protection
In the digital era, where data has become an invaluable asset, safeguarding its integrity and accessibility is paramount. The 3-2-1 rule of data backup serves as a robust strategy to ensure the resilience of your critical information in the face …
Bitdefender: Your Trusted Partner in Online Security
As the digital age accelerates, so does the need for reliable and effective cybersecurity solutions. Bitdefender Internet Security stands out as the undisputed leader in online protection, providing peace of mind and safeguarding your digital presence. Trusted by millions of …
McAfee’s Decline: A Once-Dominant Antivirus Loses Its Edge
McAfee, once a leading name in antivirus software, has experienced a significant decline in recent years. Several factors have contributed to its diminished reputation. 1. Performance Issues: McAfee’s antivirus software has been criticized for being resource-intensive, often slowing down systems, …

Harnessing Technology for Breast Cancer Awareness Month
As October rolls in, Breast Cancer Awareness Month brings communities worldwide together to focus on raising awareness and promoting early detection of breast cancer. With over 360,000 people predicted to be diagnosed with this disease in 2024 alone, it becomes …
The Decline of Norton Antivirus: Is It Still Worth It?
Norton Antivirus, once a stalwart in the realm of cybersecurity, has seen a decline in recent years. While it still offers protection, its reputation has taken a hit due to several factors. 1. Resource-Intensive: Norton’s deep scanning and real-time protection …

Debunking the Myth: PC Performance Boosters
The truth about those so-called performance enhancers. In the realm of technology, myths often persist, and one such myth revolves around PC performance boosters. These software programs claim to magically speed up your computer, but are they truly effective? Let’s …

Navigating Social Media Trends and Emerging AI Software in 2024
The social media landscape is evolving rapidly, driven by new technologies and shifting user preferences. As we move deeper into 2024, staying on top of these changes is crucial for businesses and marketers looking to maintain a competitive edge. In …

Social Engineering: The Art of Manipulation
Social engineering is a type of attack that exploits human psychology to gain access to confidential information or systems. It’s a technique that relies on manipulating people into revealing sensitive data or performing actions that can compromise their security. Unlike …
